Toyota confirms breach after Medusa ransomware threatens to leak data
Toyota Financial Services (TFS) has confirmed that it detected unauthorized access on some of its systems in Europe and Africa after Medusa ransomware claimed an attack on the company.
Toyota Financial Services, a subsidiary of Toyota Motor Corporation, is a global entity with a presence in 90% of the markets where Toyota sells its cars, providing auto financing to its customers.
Earlier on November 16, the Medusa ransomware gang listed TFS to its data leak site on the dark web, demanding a payment of $8,000,000 to delete data allegedly stolen from the Japanese company.
The threat actors gave Toyota 10 days to respond, with the option to extend the deadline for $10,000 per day.
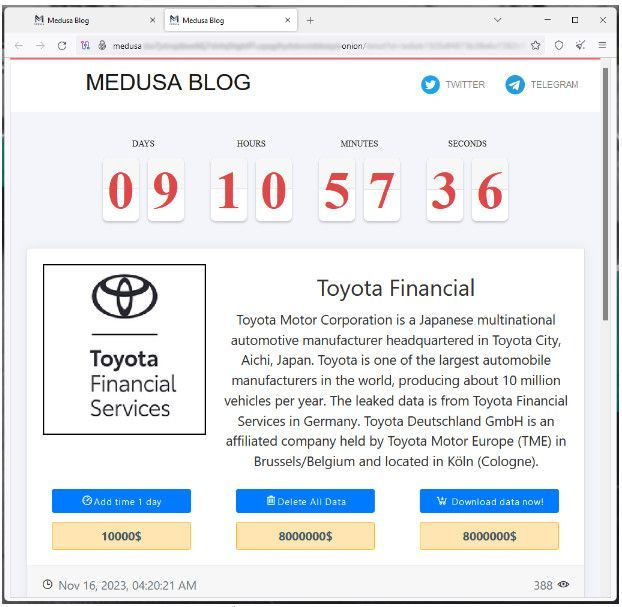
Medusa demanding $8 million from Toyota (BleepingComputer)
While Toyota Finance did not confirm if data was stolen in the attack, the threat actors claim to have exfiltrated files and threaten with a data leak if a ransom is not paid.
To prove the intrusion, the hackers published sample data that includes financial documents, spreadsheets, purchase invoices, hashed account passwords, cleartext user IDs and passwords, agreements, passport scans, internal organization charts, financial performance reports, staff email addresses, and more.
Medusa also provides a .TXT file with the file tree structure of all the data they claim to have stolen from Toyota’s systems.
Most of the documents are in German, indicating that the hackers managed to access systems serving Toyota’s operations in Central Europe.
BleepingComputer reached out to the Japanese automaker for a comment on the leaked data and a company spokesperson provided the following statement:
“Toyota Financial Services Europe & Africa recently identified unauthorized activity on systems in a limited number of its locations.”
“We took certain systems offline to investigate this activity and to reduce risk and have also begun working with law enforcement.”
“As of now, this incident is limited to Toyota Financial Services Europe & Africa.”
Regarding the status of the impacted systems and their estimated return to normal operations, the spokesperson told us that the process of bringing systems back online is already underway in most countries.
Another Citrix Bleed breach?
Earlier on November 16, following Medusa’s disclosure of TFS as their victim, security analyst Kevin Beaumont highlighted that the firm’s German office had an internet-exposed Citrix Gateway endpoint which had not been updated since August 2023, indicating that it was vulnerable to the critical Citrix Bleed (CVE-2023-4966) security issue.
A few days back, it was confirmed that Lockbit ransomware operatives were using publicly available exploits for Citrix Bleed to achieve breaches against the Industrial and Commercial Bank of China (ICBC), DP World, Allen & Overy, and Boeing.
It is possible that other ransomware groups have started to exploit Citrix Bleed, taking advantage of the massive attack surface estimated to count several thousand endpoints.
Source: bleepingcomputer.com






