USB drive malware attacks spiking again in first half of 2023
What's old is new again, with researchers seeing a threefold increase in malware distributed through USB drives in the first half of 2023
A new report by Mandiant outlines how two USB-delivered malware campaigns have been observed this year; one named 'Sogu,' attributed to a Chinese espionage threat group 'TEMP.HEX,' and another named 'Snowydrive,' attributed to UNC4698, which targets oil and gas firms in Asia.
Previously, in November 2022, the cybersecurity company highlighted a China-nexus campaign leveraging USB devices to infect entities in the Philippines with four distinct malware families.
Also, in January 2023, Palo Alto Network's Unit 42 team uncovered a PlugX variant that could hide in USB drives and infect Windows hosts they're connected to.
The Sogu campaign
Mandiant reports that Sogu is currently the most aggressive USB-assisted cyber-espionage campaign, targeting many industries worldwide and attempting to steal data from infected computers.
The victims of Sogu malware are located in the United States, France, the UK, Italy, Poland, Austria, Australia, Switzerland, China, Japan, Ukraine, Singapore, Indonesia, and the Philippines.
Most victims belong to the pharmaceutical, IT, energy, communications, health, and logistics sectors, but there are victims across the board.
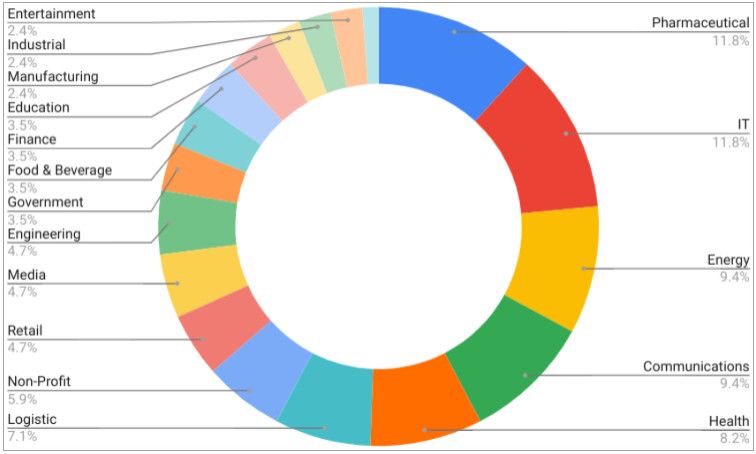
Sogu's targets (Mandiant)
The payload, called 'Korplug,' loads C shellcode (Sogu) into memory via DLL order hijacking, which requires tricking the victim into executing a legitimate file.
Sogu establishes persistence by creating a registry Run key and uses Windows Task Scheduler to ensure it runs regularly.
Next, the malware drops a batch file onto 'RECYCLE.BIN' that helps with system reconnaissance, scanning the infected machine for MS Office documents, PDFs, and other text files that may contain valuable data.
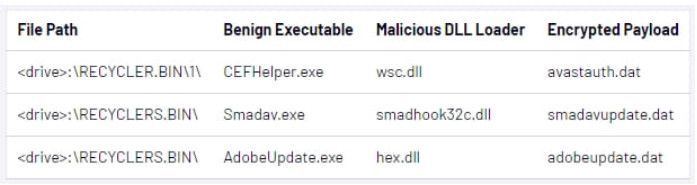
Files used by Sogu malware (Mandiant)
Files found by Sogu are copied to two directories, one on the host's C:\ drive and one on the working directory on the flash drive, and encrypted using base64.
The document files are eventually exfiltrated to the C2 server over TCP or UDP, using HTTP or HTTPS requests.

Sogu attack chain (Mandiant)
Sogu also supports command execution, file execution, remote desktop, snapping screenshots from the infected computer, setting up a reverse shell, or performing keylogging.
Any drives connected to the infected system will automatically receive a copy of Sogu's initial compromise file set to allow lateral movement.
Snowydrive campaign
Snowydrive is a campaign that infects computers with a backdoor allowing the attackers to execute arbitrary payloads through the Windows command prompt, modify the registry, and perform file and directory actions.
In this case, too, the victim is tricked into launching a legitimate-appearing executable on a USB drive, which triggers the extraction and execution of the malware's components that lie in a 'Kaspersky' folder.
The components undertake specific roles such as establishing persistence on the breached system, evading detection, dropping a backdoor, and ensuring malware propagation through newly connected USB drives.
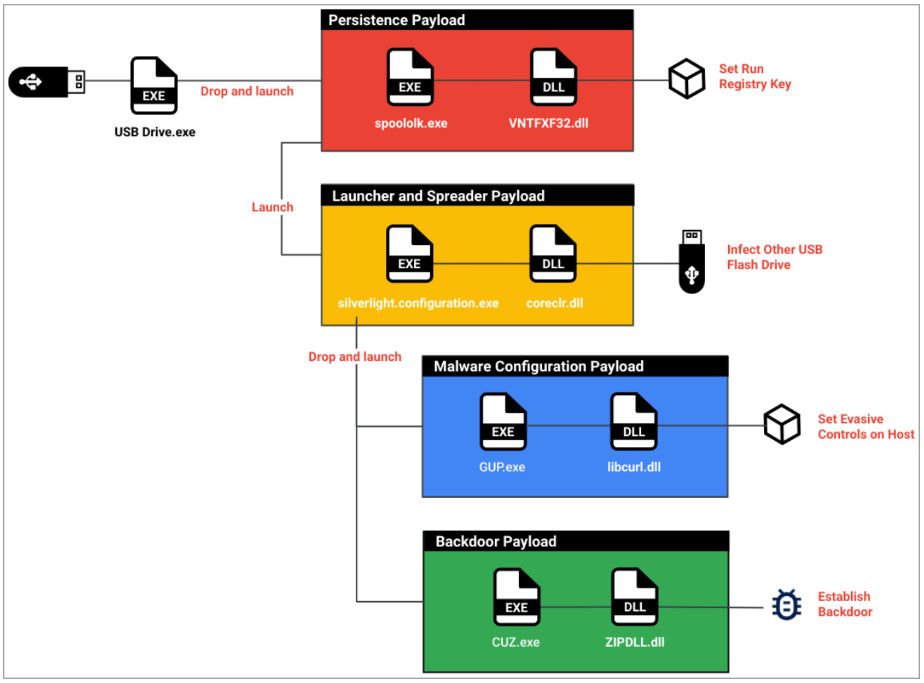
Snowydrive's components (Mandiant)
Snowydrive is a shellcode-based backdoor that is loaded into the process of 'CUZ.exe,' which is a legitimate archive unzip software.
The backdoor supports many commands that allow file operations, data exfiltration, reverse shell, command execution, and reconnaissance.
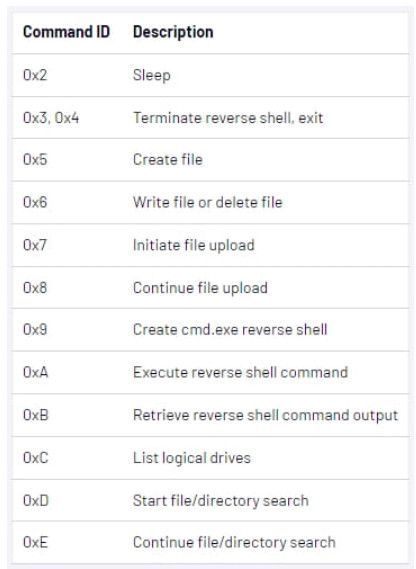
Commands supported by Snowydrive (Mandiant)
For evasion, the malware uses a malicious DLL side-loaded by 'GUP.exe,' a legitimate Notepad++ updater, to hide file extensions and specific files marked with "system" or "hidden."
USB-based attacks to continue
While USB attacks require physical access to the target computers to achieve infection, they have unique advantages that keep them both relevant and trending in 2023, as Mandiant reports.
The advantages include bypassing security mechanisms, stealth, initial access to corporate networks, and the ability to infect air-gapped systems isolated from unsecured networks for security reasons.
Mandiant's investigation point to print shops and hotels as infection hotspots for USB malware.
Still, considering the random, opportunistic spread of these backdoors, any system with a USB port could be a target.
Source: bleepingcomputer.com






